- Asking for Copies: Enables requestors to obtain unencrypted copies of specific data from Personal Data Accounts (PDAs) for asynchronous analysis, compliance, or profile building.
- One Time Read: Allows for a single, real-time access to unencrypted user data in PDAs, ideal for immediate processing or validation, with no further access thereafter.
- Conditional Verification: Facilitates the verification of certain criteria within PDAs, such as age verification, based on predefined conditions, with Zero-Knowledge (ZK) proof enhancements planned.
- Blind Computation (In Development): Explores secure computation methods on encrypted data, preserving user privacy without decryption.
Example:
Let’s bring Data Requests to life with a real-world example.
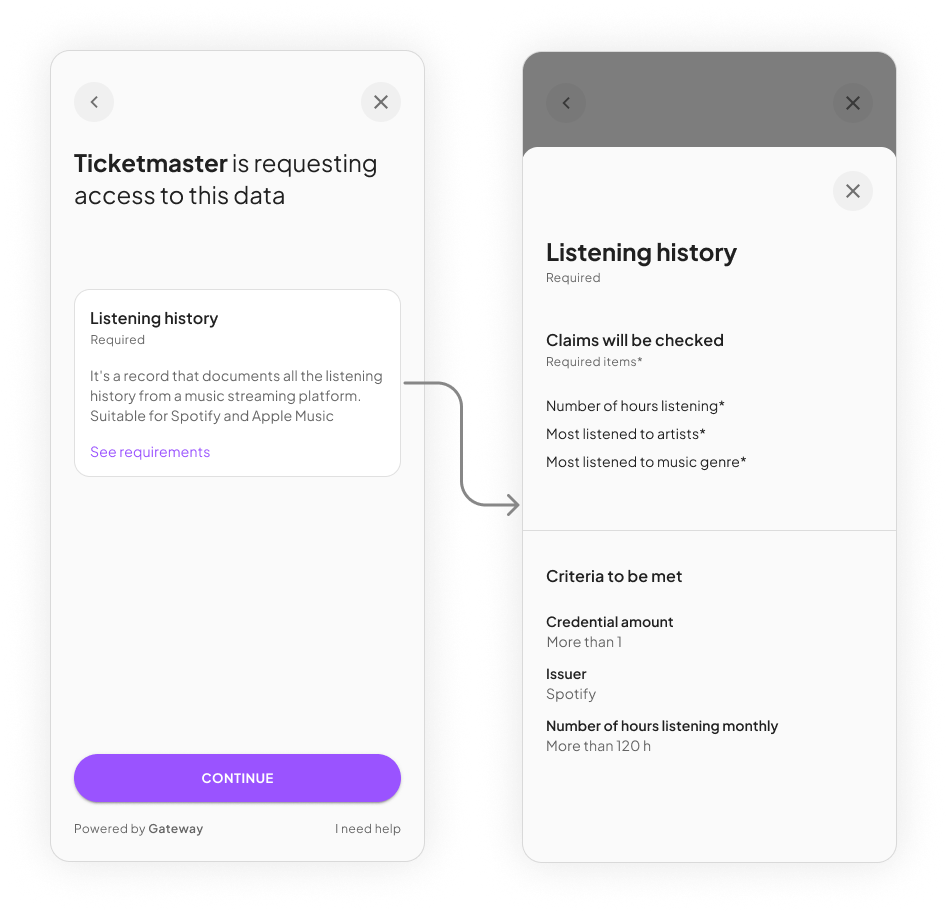
Request Lifecycle
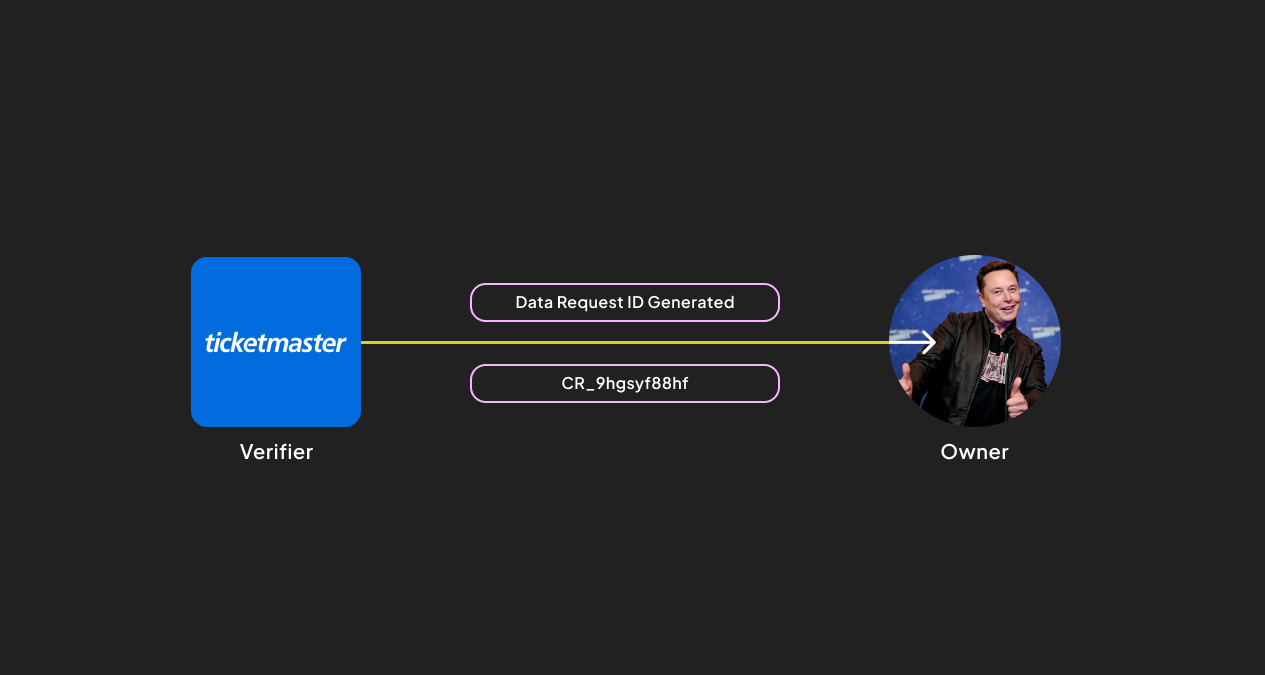
Data requests are exclusively exchanged between the Owner and the Requestor. The Request’s lifecycle depends on the Owner’s response or lack thereof.The Requestor sends a Data Request
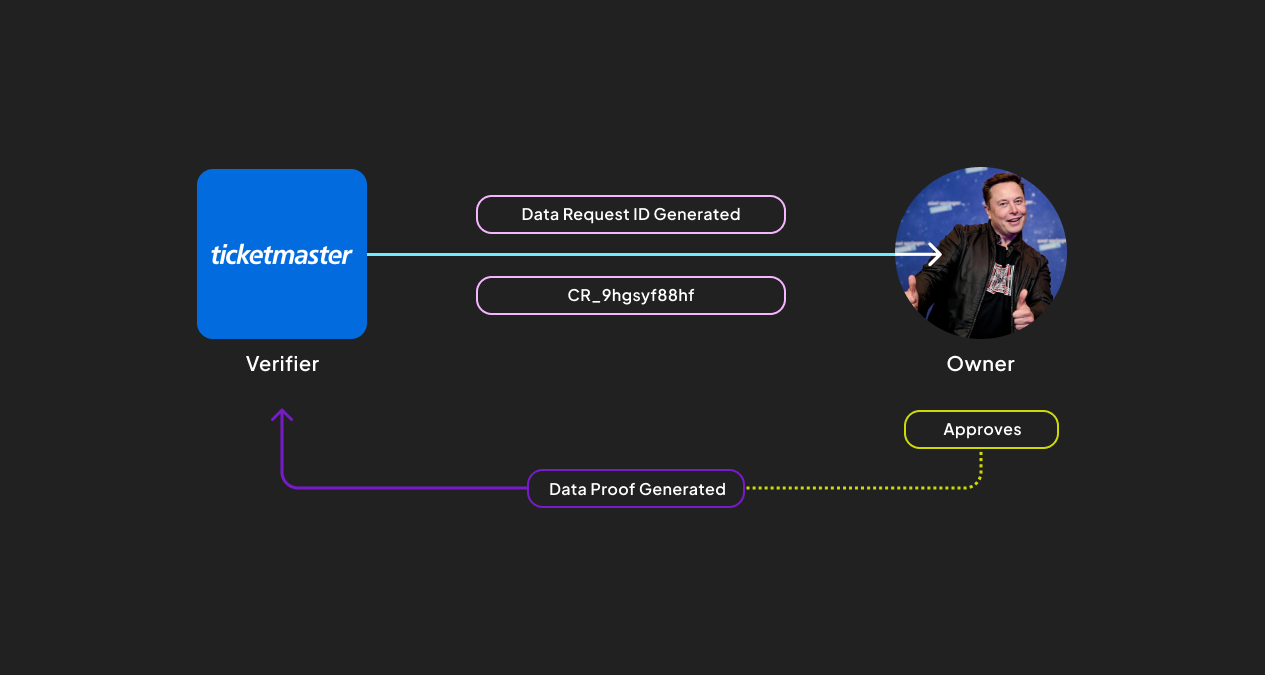
Acceptance: Owner Accepts the Request
Reject: Owner Rejects the Request
If the owner sees the request and is uncomfortable/uninterested, they can reject it. The request status would be changed to “Rejected,” and the Request would not be closed. No Data Proof would be generated, and the verifier would see this as a “Rejected” request on their dashboard.Expired: Owner Does Not Take Action
If the owner does not explicitly choose to accept or reject, the Data Request will be marked as “Expired” after 3 days of no action. This Request is now closed.Request structure
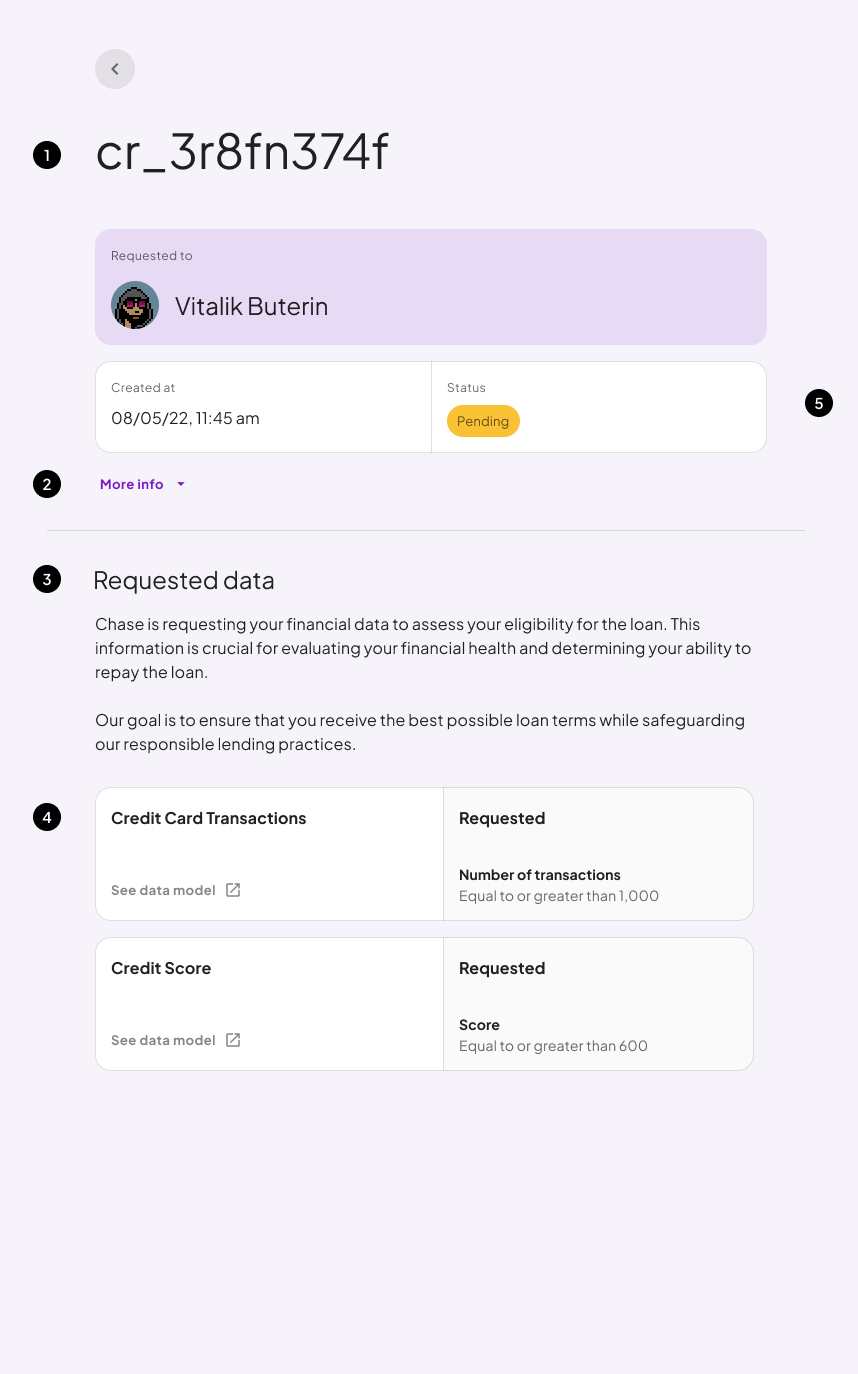
1. Data Request Template ID
Each Data Request is inherently linked to its originating Template ID, streamlining the process of filtering, indexing, and identifying the most frequently used templates.2. ID
Each Data Request has an associated UUID that is unique between the owner requesting the information and the verifier asking.No two Requests will ever share the same DR ID.
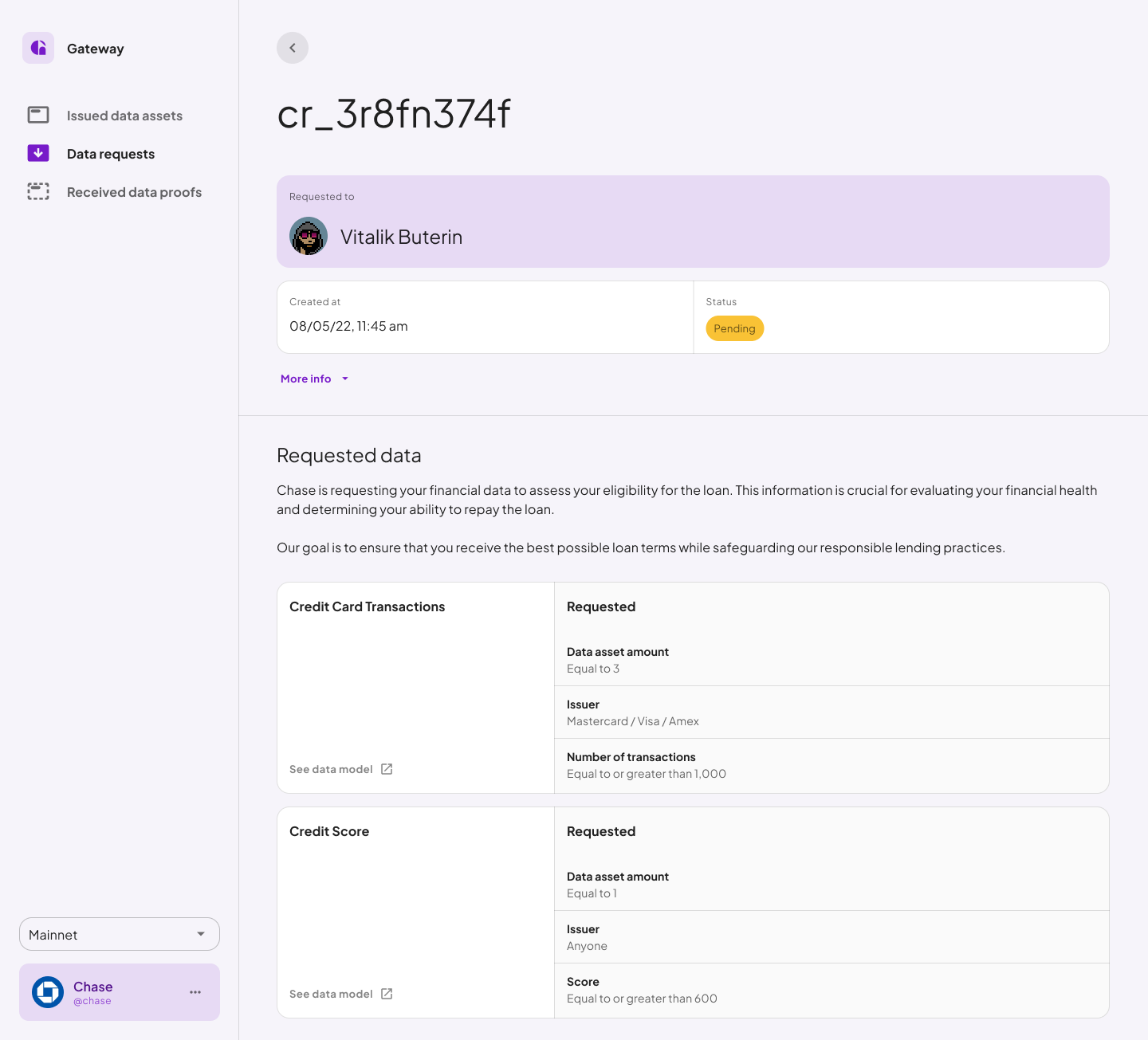
3. Requested Data
As a verifier, the data you request hinges on the Data Request Template you’ve selected. Make sure to choose a template ID that aligns precisely with your needs to ensure the information you receive is both relevant and useful.4. Data Use
Verifiers are required to specify the intended use of the requested data. This transparency is crucial, enabling the owner to fully grasp the implications and potential benefits of granting permission.5. Status
Every Data Request carries a specific status that dictates the actions an owner can take, as previously outlined. For a quick refresher, consult the table below: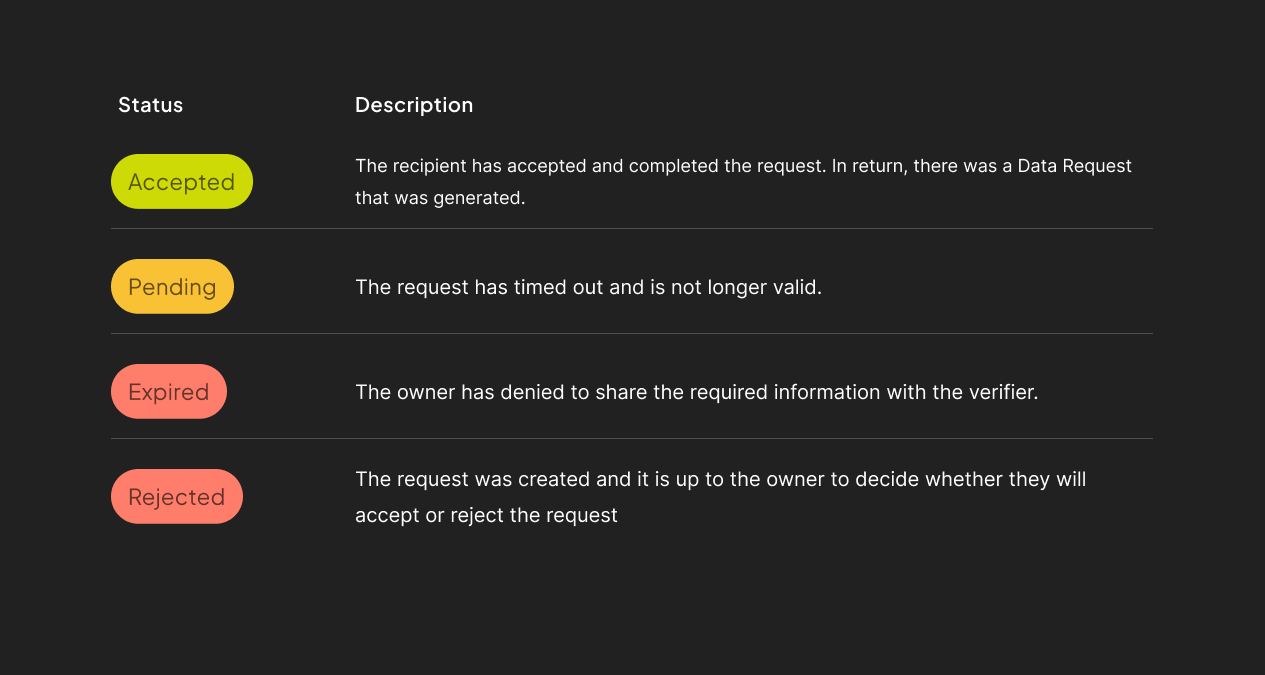
Managing Requests
Users and Organizations can see and control their requests from the Gateway Dashboard.