
🌐 Remember: Data Proofs are static information pieces about 1 or more PDAs
that the owner holds.
⚠️ Gateway Protocol will be adding the revocability of proofs natively soon! At the moment, proofs are not revokable.
Parties Involved
Consent Management
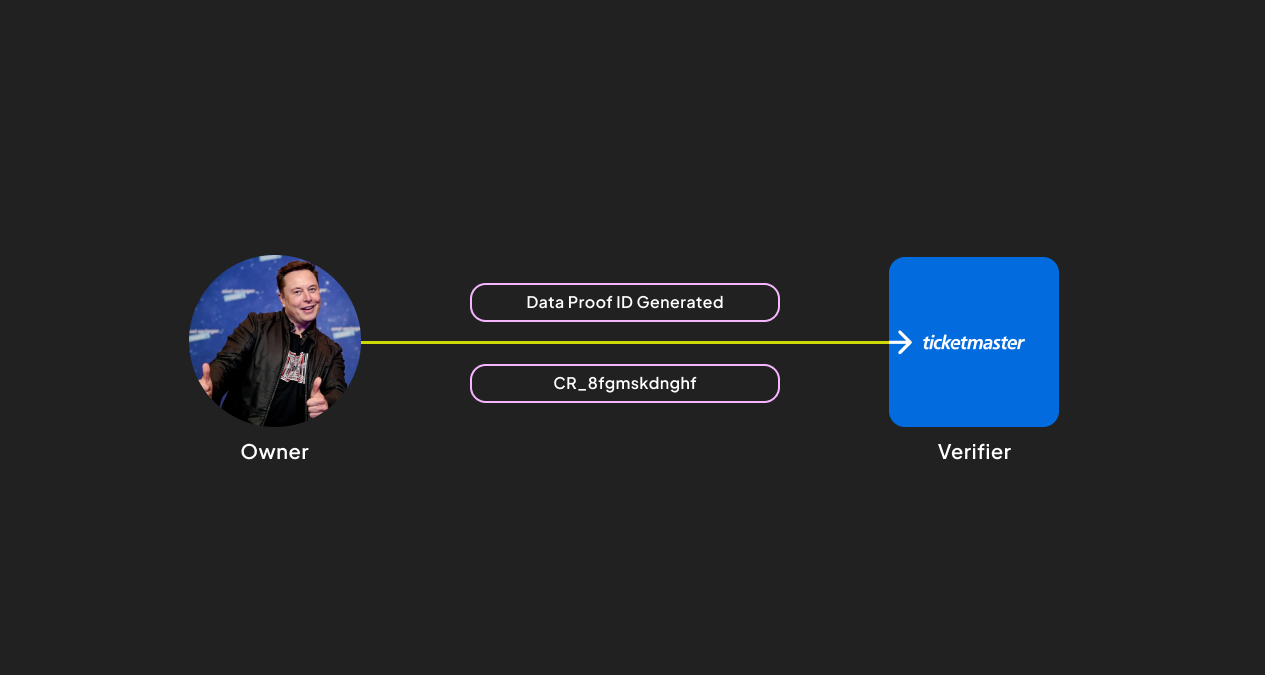
To ensure compliance with GDPR and other leading privacy regulations, for Data Proof to be conditioned, there must be explicit consent from the owner for the verifier to access the data. Gateway Protocol records this consent as a transaction on Arweave, so it is permanently verifiable. The consent is given as a non-reputable cryptographic signature generated by the user’s wallet. This consent, along with the request ID, is recorded on Arweave to create permanence and easy reference for the verifier and owner to check against the consent given at any point.UUID
Data Proof Status
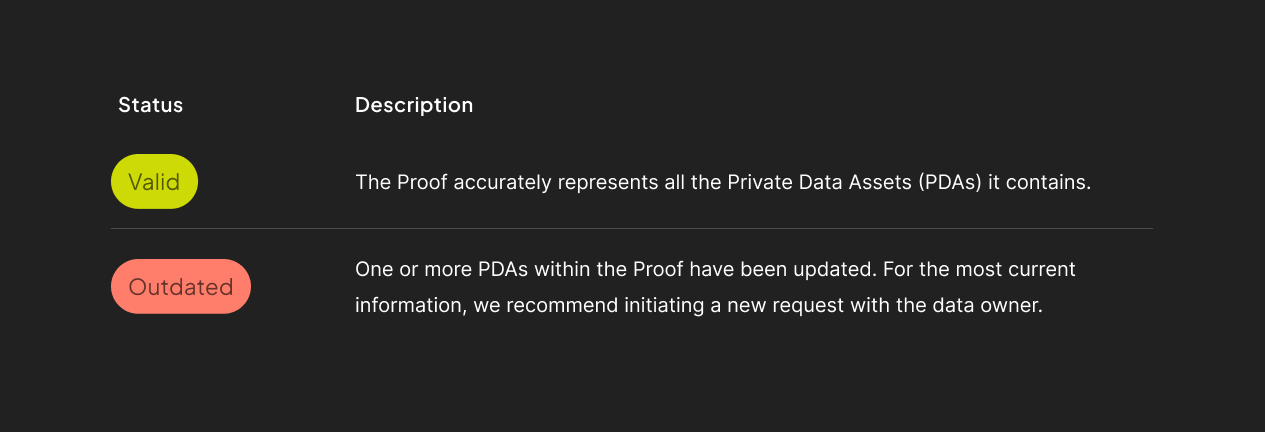
⚠️ Relying on outdated information can be risky, especially if you expect that
data to remain accurate. It’s important to note that issuers cannot be held
responsible for any issues arising from using outdated proof data, as its
accuracy is no longer guaranteed.”
How is it structured?
Private Data Assets (PDAs) are categorized by their data model ID in a Data Proof. While a Data Proof will always contain at least one PDA, the number can vary based on the owner’s discretion and the specifications of the Data Request, if applicable. Verifiers can access the PDA data using the API or the dashboard.Other Pieces
Each Data Proof also contains information about:- Data Request (if any)
- Data Request Template (if any)
- Timestamp of Proof Creation
Cost Burden
The cost structure for a Data Proof is both clear and uncomplicated. It’s calculated as follows:Total Cost => i = 1∑N(Cost Per PDA for Data Model i * Number of PDAs from Data Model i) + Gateway Facilitation FeeFor instance, if a Data Proof includes three PDAs from the ‘Credit Card Transaction’ Data Model, each costing $0.10, and two PDAs from the ‘Credit Score’ Data Model, each costing 0.20 USD. Gateway adds a 5% facilitation fee to the sum. The total cost for this Data Proof would, therefore be:
((3*0.20))*1.05=$0.735In this example, the issuers of the PDAs would collectively receive 0.035. The per-PDA cost for each Data Model is readily available for reference. To enhance the predictability of Data Request costs, we include the average cost of fulfilling a request—also known as the ‘proof cost’—right within the Data Request Template. This way, you get a clear financial picture upfront, streamlining your planning and decision-making processes.
Verifier Requests Information
If the verifier receives the Proof through a request they made, they are responsible for paying the cost. This will be invoiced to them on a monthly basis. To learn how Verifiers can make requests, click here.Owner Sends to Verifier
If the Owner sends the Proof without an associated Data Request, the Recipient is responsible for paying the cost of the Proof.Privacy + Security
Gateway takes privacy and security of the underlying data you own quite seriously. To ensure that only the verifier (receiving party) is the one seeing the information, Data Proofs employ a two-tier encryption strategy for enhanced security. Initially, the data is encrypted using a one-time symmetric key, which ensures fast and efficient encryption. This symmetric key itself is then encrypted using the intended recipient’s public key. This approach marries the speed of symmetric encryption with the security of public-key encryption, making sure that only the intended recipient, who possesses the corresponding private key, can decrypt the symmetric key and, by extension, the data. This dual-layer encryption not only enhances security but also ensures that the data remains confidential and accessible solely by the designated user. Reasons for this approach include: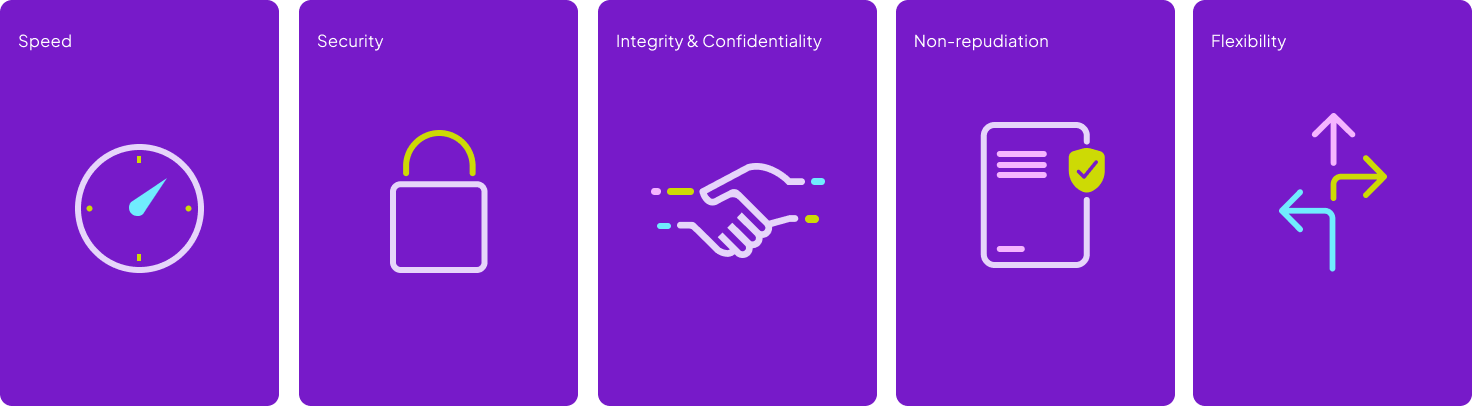
- Speed: Symmetric encryption is generally faster than public-key encryption, making it ideal for encrypting any size proof - even ones that may contain hundreds of PDAs.
- Security: By subsequently using public-key encryption for the symmetric key, the data gains an additional layer of security. This also ensures that even if the symmetric key is compromised, the data remains secure unless the recipient’s private key is also compromised.
- Integrity and Confidentiality: The usage of the recipient’s public key ensures that the data can only be decrypted by the intended recipient, thus maintaining both the integrity and the confidentiality of the data.
- Non-repudiation: Encrypting with the recipient’s public key also provides a layer of non-repudiation, as only the intended recipient could have decrypted the data.
- Flexibility: This two-tier approach can be easily adapted to various data types and transmission protocols, making it versatile for different use cases.

